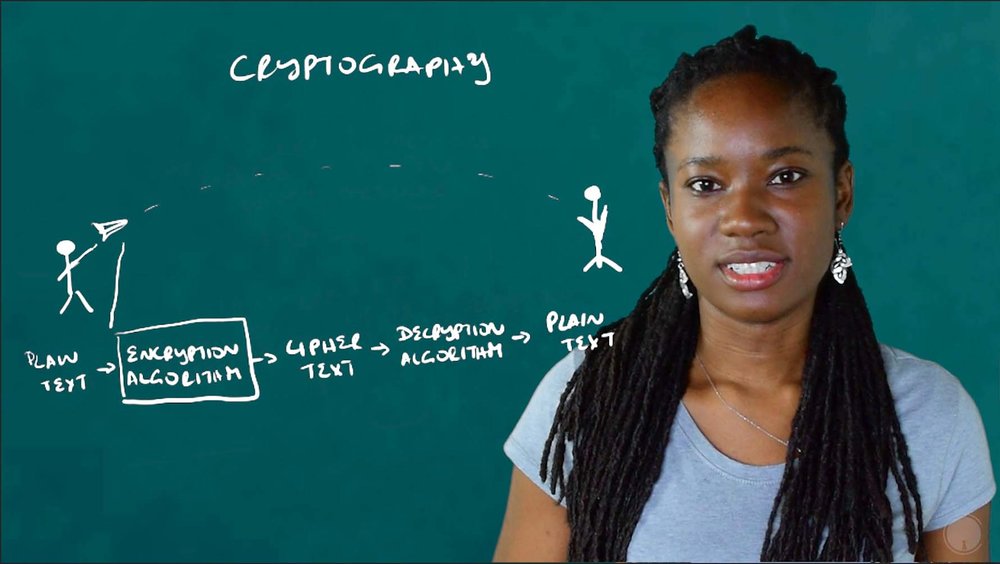INTRODUCTION TO THE PRIVACY COIN GUIDE
If you’re looking for a quick and easy way to assess what the best privacy coin in the current space is, which has the best features, or which is most likely to give high returns, then this is not that guide. My goal is to give you the power to make your own decisions, to clearly state my biases, and educate. I really wanted to understand this niche of the crypto-space due to my background and current loyalties[1], and grasp the nuances of the features, origins and timelines of technologies used in privacy coins, while not being anything close to a developer myself. This is going to be a 3-part series, starting with an overview and basic review of the technology, then looking at its implications, and ending with why I like a specific project. It might be mildly interesting or delightfully educational. Cryptocurrencies are young and existing privacy coins are deploying technology that is a work in progress. This series assumes a basic understanding of how blockchains work, specifically as used in cryptocurrencies. If you don’t have that understanding, might I suggest that you get it? [2],[3],[4] Because cryptocurrencies have a long way to go before reaching their end-game: when the world relies on the technology without understanding it. So, shall we do a deep dive into the privacy coin space?
FIRST THERE WAS BITCOIN
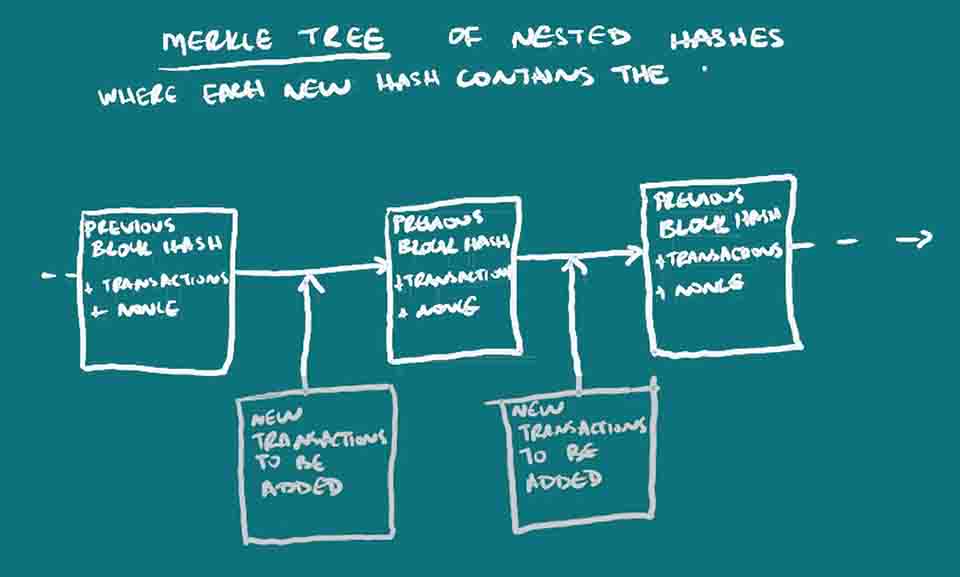
Cryptocurrencies allow you to tokenize value and track its exchange between hands over time, with transaction information verified by a distributed network of users. The most famous version of a cryptocurrency in use is Bitcoin, defined as peer-to-peer electronic cash. [5] Posted anonymously in 2008, the whitepaper seemed to be in direct response to the global financial meltdown and public distrust of the conventional banking and financing systems. Although cryptographic techniques are used in Bitcoin to ensure that (i) only the owner of a specific wallet has the authority to spend funds from that wallet, (ii) the public address is linked but cannot be traced by a third party to the private address (iii) the information is stored via cryptographic hashing in a merkle tree structure to ensure data integrity, the actual transaction information is publicly visible on the blockchain and can be traced back to the individual through chain analysis.[6] This has raised fears of possible financial censorship or the metaphorical tainting of money due to its origination point, as demonstrated in the Silk Road marketplace disaster.[7] This can happen because fiat money is usually exchanged for cryptocurrency at some point, as crypto-enthusiasts are born in the real world and inevitably cash out. There are already chain analysis firms and software that are increasingly efficient at tracking transactions on the Bitcoin blockchain.[8] This lack of privacy is one of the limitations of Bitcoin that has resulted in the creation of altcoins that experiment with the different features a cryptocurrency can have. Privacy coins are figuring out how to introduce privacy in addition to the payment network. The goal is to make the cryptocurrency fungible, each unit able to be exchanged for equal value without knowledge of its transaction history – like cash, while being publicly verifiable on a decentralized network. In other words, anyone can add the math up without being able to see the full details. Some privacy solutions and protocols have popped up as a result:
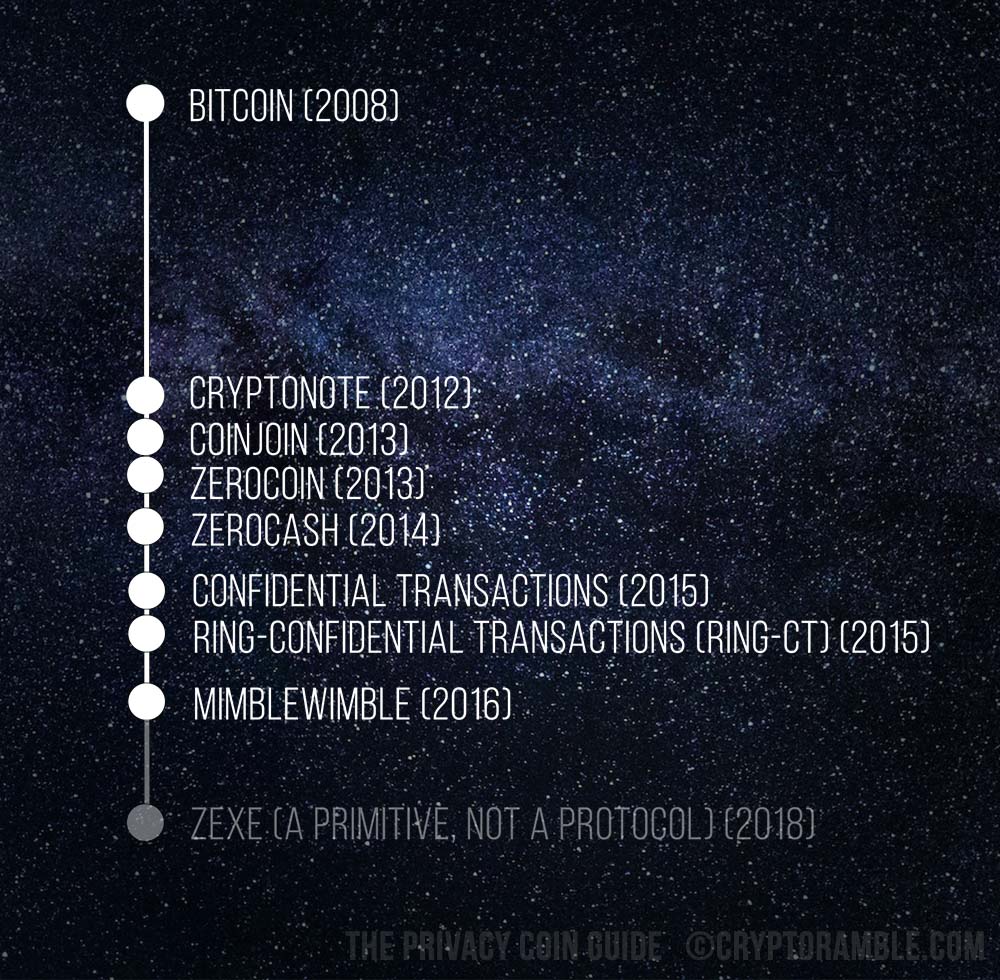
CRYPTONOTE – Ring Signatures and Stealth Addresses
Used in: Monero and Particl as its successor RING-CT, Bytecoin
In December 2012, CryptoNote introduced the use of ring signatures and stealth addresses (along with other notable features such as its own codebase) to improve cryptocurrency privacy.[9] An updated CryptoNote version 2 came in October 2013 [10](though there is some dispute over this timeline [11]), also authored under the name Nicolas van Saberhagen. Ring signatures hide sender information by having the sender sign a transaction using a signature that could belong to multiple users. This makes a transaction untraceable. Stealth addresses allow a receiver to give a single address which generates a different public address for funds to be received at each time funds are sent to it. That makes a transaction unlinkable. In terms of privacy, CryptoNote gave us a protocol for untraceable and unlinkable transactions. The first implementation of CryptoNote technology was Bytecoin in March 2014 (timeline disputed [12]), which spawned many children (forks) in subsequent years, a notable example being Monero, based on CryptoNote v2 in April 2014.
RING SIGNATURES and STEALTH ADDRESSES
PROS
– Provides sender and receiver privacy
– Privacy can be default
– Mature technology
– Greater scalability with bulletproofs
– Does not require any third-party
CONS
– Privacy not very effective without high volume
-Does not hide transaction information if not combined with another protocol.
COINJOIN
Used in: Dash
Bitcoin developer Gregory Maxwell proposed a set of solutions to bring privacy to Bitcoin and cryptocurrencies, the first being CoinJoin (January 28 – Aug 22, 2013).[13],[14] CoinJoin (sometimes called CoinSwap) allows multiple users to combine their transactions into a single transaction, by receiving inputs from multiple users, and then sending their outputs to the multiple users, irrespective of who in the group the inputs came from. So, the receiver will get whatever output amount they were supposed to, but it cannot be directly traced to its origination input. Similar proposals include Coinshuffle in 2014 and Tumblebit in 2016, building on CoinJoin but not terribly popular [15],[16]. They fixed the need for a trusted third party to ‘mix’ the transactions. There are CoinJoin implementations that are being actively worked on but are not the most popular privacy solutions of today. A notable coin that uses CoinJoin technology is Dash, launched in January 2014, with masternodes in place of a trusted party.
COINJOIN
PROS
– Provides sender and receiver privacy
– Easy to implement on any cryptocurrency
– Lightweight
– Greater scalability with bulletproofs
– Mature technology
CONS
– Least anonymous privacy solution. Transaction amounts can be calculated
– Even without third-party mixer, depends on wealth centralization of masternodes
ZEROCOIN
Used in: Zcoin, PIVX
In May 2013, the Zerocoin protocol was introduced by John Hopkins University professor Matthew D. Green and his graduate students Ian Miers and Christina Garman.[17] In response to the need for use of a third party to do CoinJoin, the Zerocoin proposal allowed for a coin to be destroyed and remade in order to erase its history whenever it is spent. Zero-knowledge cryptography and zero-knowledge proofs are used to prove that the new coins for spending are being appropriately made. A zero-knowledge proof allows one party to prove to another that they know specific information, without revealing any information about it, other than the fact that they know it. Zerocoin was not accepted by the Bitcoin community as an implementation to be added to Bitcoin, so a new cryptocurrency had to be formed. Zcoin was the first cryptocurrency to implement the Zerocoin protocol in 2016. [18]
ZEROCOIN
PROS
– Provides sender and receiver privacy
– Supply can be audited
– Relatively mature technology
– Does not require a third-party
CONS
– Requires trusted setup (May not be required with Sigma protocol)
– Large proof sizes (not lightweight)
– Does not provide full privacy for transaction amounts
ZEROCASH
Used in: Zcash, Horizen, Komodo, Zclassic, Bitcoin Private
In May 2014, the current successor to the Zerocoin protocol, Zerocash, was created, also by Matthew Green and others (Eli Ben-Sasson, Alessandro Chiesa, Christina Garman, Matthew Green, Ian Miers, Eran Tromer, Madars Virza).[19] It improved upon the Zerocoin concept by taking advantage of zero-knowledge proofs called zk-snarks (zero knowledge succinct non-interactive arguments of knowledge). Unlike Zerocoin, which hid coin origins and payment history, Zerocash was faster, with smaller transaction sizes, and hides transaction information on the sender, receiver and amount. Zcash is the first cryptocurrency to implement the Zerocash protocol in 2016. [20]
ZEROCASH
PROS
– Provides full anonymity. Sender, receiver and amount hidden.
– Privacy can be default?
– Fast due to small proof sizes.
– Payment amount can be optionally disclosed for auditing
– Does not require any third-party
CONS
– Requires trusted setup. (May be improved with zt-starks technology)
– Supply cannot be audited. And coins can potentially be forged without proper implementation.
– Private transactions computationally intensive (improved with Sapling upgrade)
CONFIDENTIAL TRANSACTIONS
Used in: Monero and Particl with Ring Signatures as RING-CT
The next proposal from Maxwell was that of confidential transactions, proposed in June 2015 as part of the Sidechain Elements project from Blockstream, where Maxwell was Chief Technical Officer.[21],[22] It proposed to hide the transaction amount and asset type (e.g. deposits, currencies, shares), so that only the sender and receiver are aware of the amount, unless they choose to make the amount public. It uses homomorphic encryption[23] to encrypt the inputs and outputs by using blinding factors and a kind of ring signature in a commitment scheme, so the amount can be ‘committed’ to, without the amount actually being known. I’m terribly sorry if you now have the urge to go and research exactly what that means. The takeaway is that the transaction amount can be hidden from outsiders while being verifiable.
CONFIDENTIAL TRANSACTIONS
PROS
– Hides transaction amounts
– Privacy can be default
– Mature technology
– Does not require any third-party
CONS
– Only provides transaction amount privacy when used alone
RING-CT
Used in: Monero, Particl
Then came Ring Confidential transactions, proposed by Shen-Noether of Monero Research Labs in October 2015.[24] RingCT combines the use of ring signatures for hiding sender information, with the use of confidential transactions (which also uses ring signatures) for hiding amounts. The proposal described a new type of ring signature, A Multi-layered Linkable Spontaneous Anonymous Group signature which “allows for hidden amounts, origins and destinations of transactions with reasonable efficiency and verifiable, trustless coin generation”.[25] RingCT was implemented in Monero in January 2017 and made mandatory after September 2017.
RING -CONFIDENTIAL TRANSACTIONS
PROS
– Provides full anonymity. Hides transaction amounts and receiver privacy
– Privacy can be default
– Mature technology
– Greater scalability with bulletproofs
– Does not require any third-party
CONS
– Privacy not very effective without high volume
MIMBLEWIMBLE
Used in: Grin
Mimblewimble was proposed in July 2016 by pseudonymous contributor Tom Elvis Jedusorand further developed in October 2016 by Andrew Poelstra.[26],[27] Mimblewimble is a “privacy and fungibility focused cryptocoin transaction structure proposal”.[28] The key words are transaction structure proposal, so the way the blockchain is built is different, in order to accommodate privacy and fungibility features. Mimblewimble uses the concept of Confidential transactions to keep amounts hidden, looks at private keys and transaction information to prove ownership of funds rather than using addresses, and bundles transactions together instead of listing them separately on the blockchain. It also introduces a novel method of pruning the blockchain. Grin is a cryptocurrency in development that is applying Mimblewimble. Mimblewimble is early in development and you can understand it more here [29].
MIMBLEWIMBLE
PROS
– Hides transaction amounts and receiver privacy
– Privacy is on by default
– Lightweight
– No public addresses?
CONS
– Privacy not very effective without high volume
– Sender and receiver must both be online
– Relatively new technology
ZEXE
Fresh off the minds of brilliant cryptographers (Sean Bowe, Alessandro Chiesa, Matthew Green, Ian Miers, Pratyush Mishra, Howard Wu), in October 2018 Zexe proposed a new cryptographic primitive called ‘decentralized private computation.[30] It allows users of a decentralized ledger to “execute offline computations that result in transactions”[31], but also keeps transaction amounts hidden and allows transaction validation to happen at any time regardless of computations being done online. This can have far reaching implications for privacy coins in the future. Consider cases where transactions need to be automatic and private, without both parties being present.
NETWORK PRIVACY
Privacy technologies that look at network privacy as nodes communicate with each other on the network are important considerations, rather than just looking at privacy on the blockchain itself. Anonymous layers encrypt and/or reroute data as it moves among peers, so it is not obvious who they originate from on the network. They are used to protect against surveillance or censorship from ISPs and governments. The Invisible Internet Project (I2P) is an anonymous network layer that uses end to end encryption for peers on a network to communicate with each other.[32] Its history dates back to 2003. Kovri is a Monero created implementation of I2P.[33] The Onion Router (Tor) is another anonymity layer [34] that Verge is a privacy cryptocurrency that uses. But its historical link to the US government may be is concerning to some[35]. Dandelion transaction relay is also an upcoming Bitcoin improvement proposal (BIP) that scrambles IP data that will provide network privacy for Bitcoin as transaction and other information is transmitted.[36],[37],[38]
UPCOMING
Monero completed bulletproofs protocol updates that reduce RINGCT transaction sizes and thus transaction fee costs. (Bulletproofs are a replacement for range proofs used in confidential transactions that aid in encrypting inputs and outputs by making sure they add to zero).
Sigma Protocol – being actively researched by Zcoin team as of 2018 to replace Zerocoin protocol so that a trusted setup is not required.[39] There is a possible replacement for zk-snarks, called zk-starks, another form of zero-knowledge proof technology, that may make a trusted set-up unnecessary for zero-knowledege proof coins.[40]
PART 1 CONCLUSION OF THE PRIVACY COIN GUIDE ON THE TECHNOLOGY BEHIND PRIVACY COINS
Although Bitcoin is still a groundbreaking technology that gives us a trust-less transaction system, it has failed to live up to its expectations of privacy. Over time, new privacy technologies have arrived and are arriving with innovative and exciting solutions for Bitcoin’s lack of fungibility. It is important to note that these technologies are built on prior research and application, but we are considering their use in cryptocurrencies. Protocols are proposed based on cryptographic concepts that show how they would work, and then developers actually implement them. Please note that I did not include the possibility of improper implementation as a disadvantage, and the advantages assume that the technical development is well done. A very important point is that coins can also adapt new privacy technologies as their merits become obvious, even as they start with a specific privacy protocol. Furthermore, I am, unfortunately, positive that this is not an exhaustive overview and I am only covering publicized solutions. Next, we’ll talk more about the pros and cons and give an idea of how the coins can be compared.

 The Truth About Altcoins
The Truth About Altcoins 


 Each cryptocurrency has its own blockchain which uses a specific kind of consensus algorithm to organize transactions in the blockchain ‘database’. The original consensus algorithm used in Bitcoin is Proof of Work, as described in my previous post
Each cryptocurrency has its own blockchain which uses a specific kind of consensus algorithm to organize transactions in the blockchain ‘database’. The original consensus algorithm used in Bitcoin is Proof of Work, as described in my previous post 
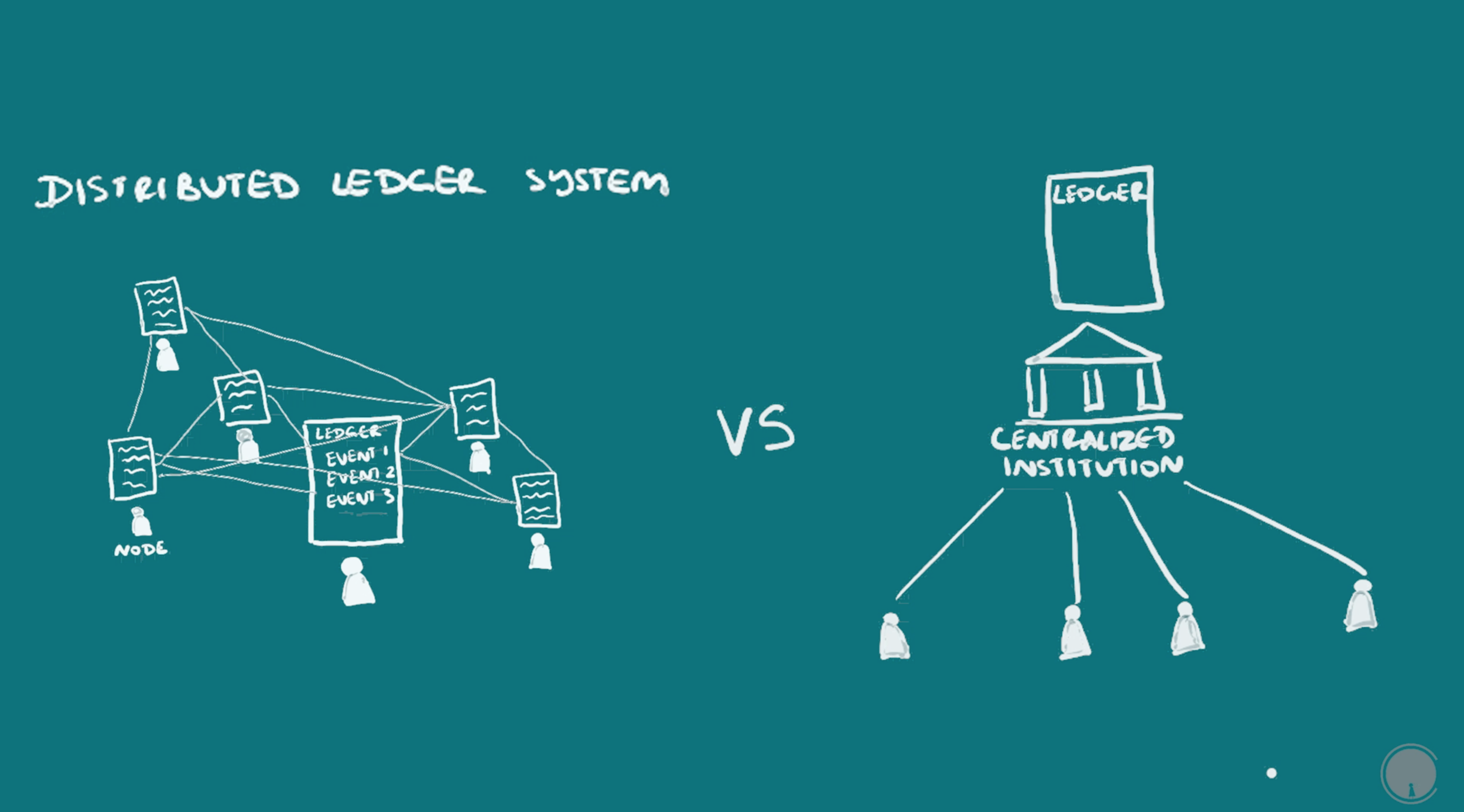
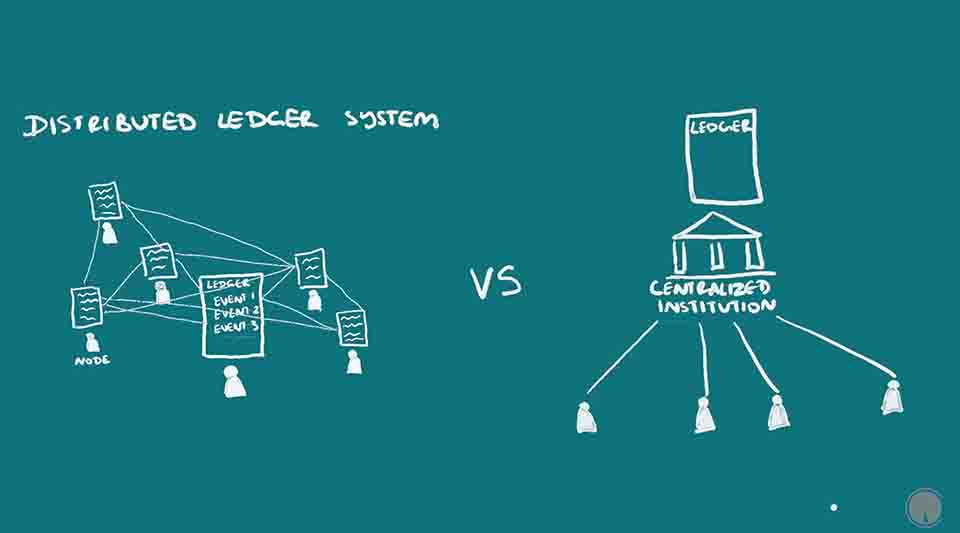 tion point called a node, usually a computer interface. The information can be updated by anyone on the network who has the right resources to do so and can be verified by all the nodes. There are ways to verify that the information recorded is accurate and make it almost impossible for those updating the blockchain to change it in their favor, much more so than the centralized ledgers that have existed in human histor
tion point called a node, usually a computer interface. The information can be updated by anyone on the network who has the right resources to do so and can be verified by all the nodes. There are ways to verify that the information recorded is accurate and make it almost impossible for those updating the blockchain to change it in their favor, much more so than the centralized ledgers that have existed in human histor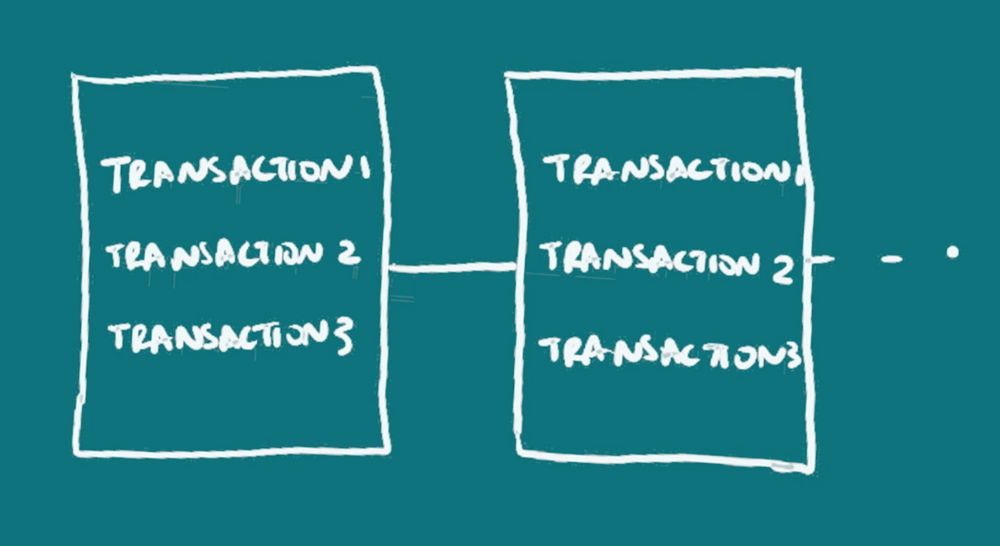
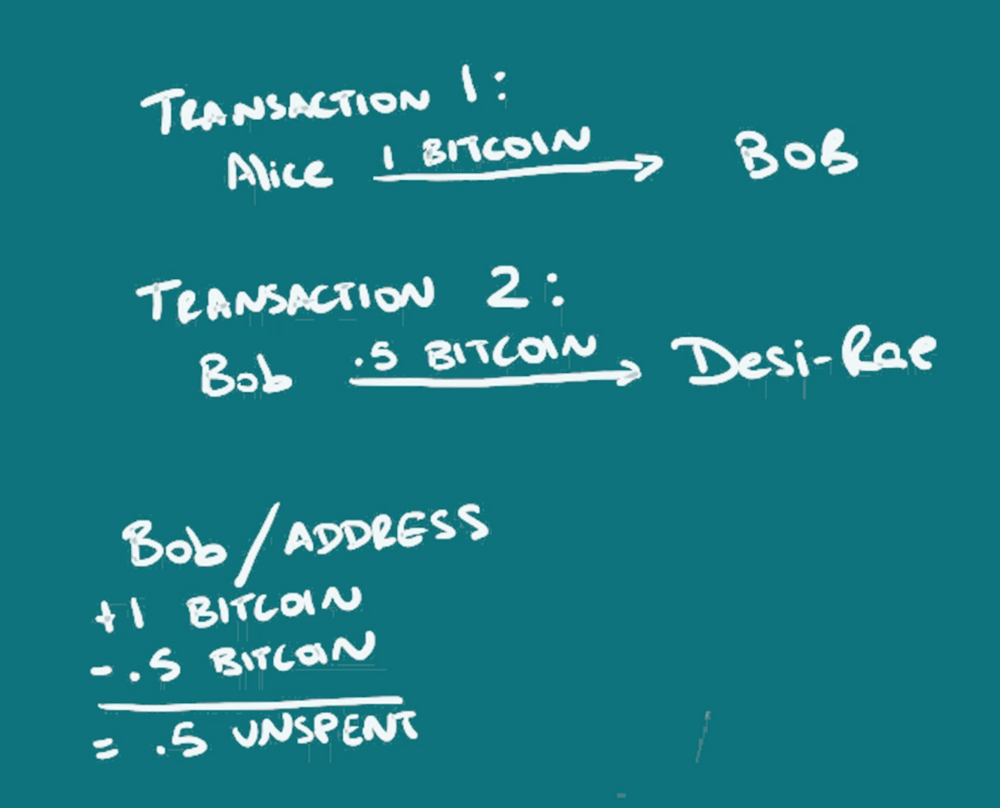
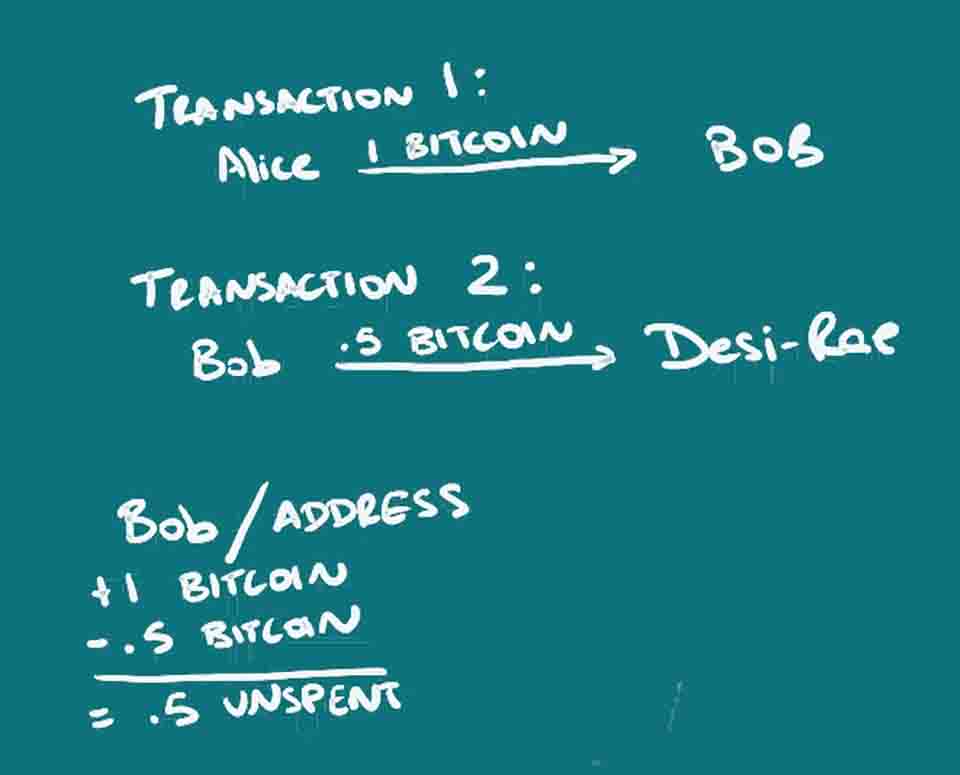 Instead of a person, an address is used, in this case a string of characters, which may or may not be able to be linked to an individual. The address is actually a key (actually a hash of a key/that’s a simplification), just one of a key-pair, something used in public-key or asymmetric cryptography. The address that is recorded on the blockchain as having sent or received funds, is the public address that someone can share, but only the owner of the other key in the pair, that’s the private key or private address, has the ability to spend the funds once received. For more information on public-key cryptography, read or watch
Instead of a person, an address is used, in this case a string of characters, which may or may not be able to be linked to an individual. The address is actually a key (actually a hash of a key/that’s a simplification), just one of a key-pair, something used in public-key or asymmetric cryptography. The address that is recorded on the blockchain as having sent or received funds, is the public address that someone can share, but only the owner of the other key in the pair, that’s the private key or private address, has the ability to spend the funds once received. For more information on public-key cryptography, read or watch 
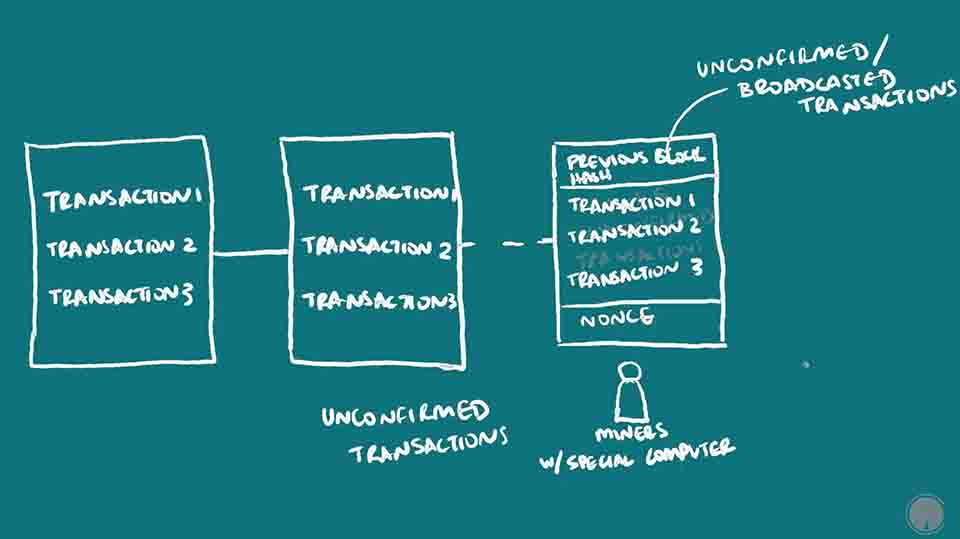
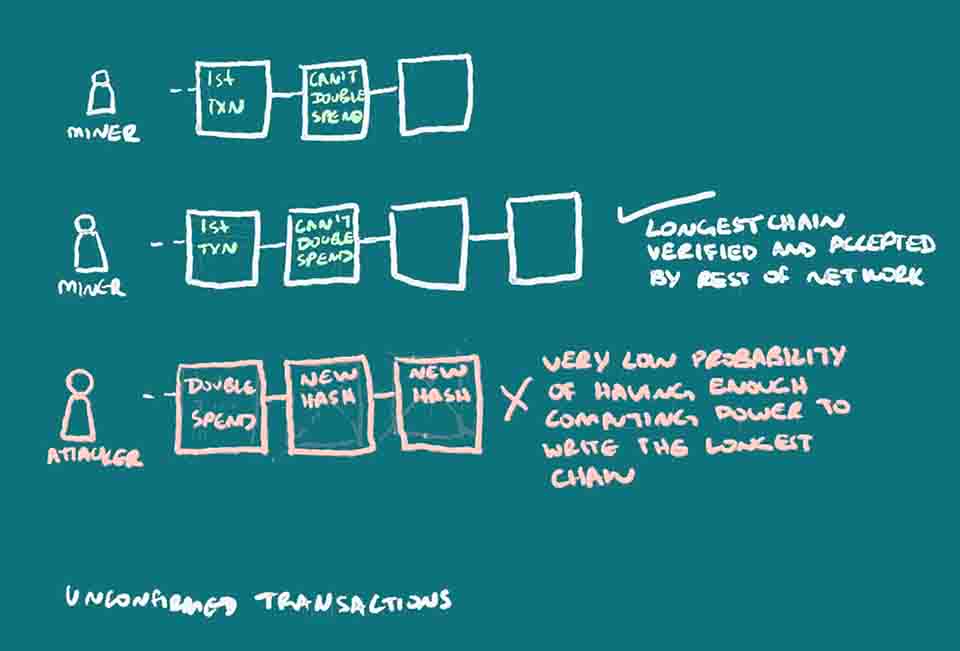
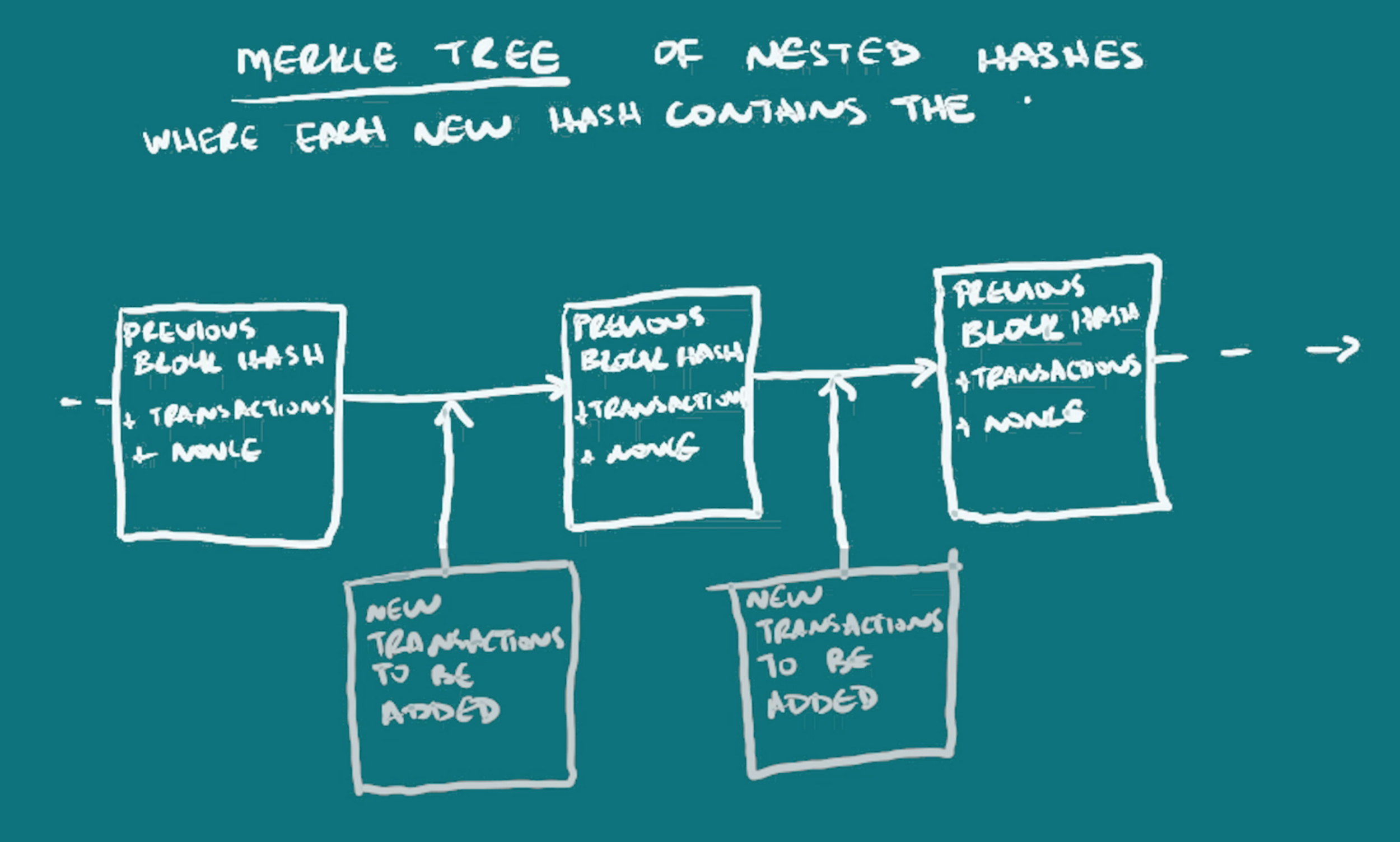 Preventing the Double-Spend Attack
Preventing the Double-Spend Attack